Attack Trees¶
Attack Trees are a simple effective way to understand what assets are at risk, the threats against them, and the associated countermeasures.
Here we use PlantUML WBS to create the tree structure, with PlantUML Styles to highlight the target, attacks, and countermeasures.
Type |
Colour |
Meaning |
|---|---|---|
AttackTarget |
Red Fill |
The Asset that is the target of Attack. This is the root of the tree. |
AttackPath |
Red Outline |
Each node is an individual Attack step. An Attack may consist of sub-branches that are different ways of implementing the parent attack step. An & symbol on an Attack node means that it must be combined with other attacks. Default is OR i.e. either one attack OR the other could be used. |
CounterMeasure |
Green Fill |
The countermeasure against the Attack. This is at the end of the branch. |
An Attack Tree for PIN Entry¶
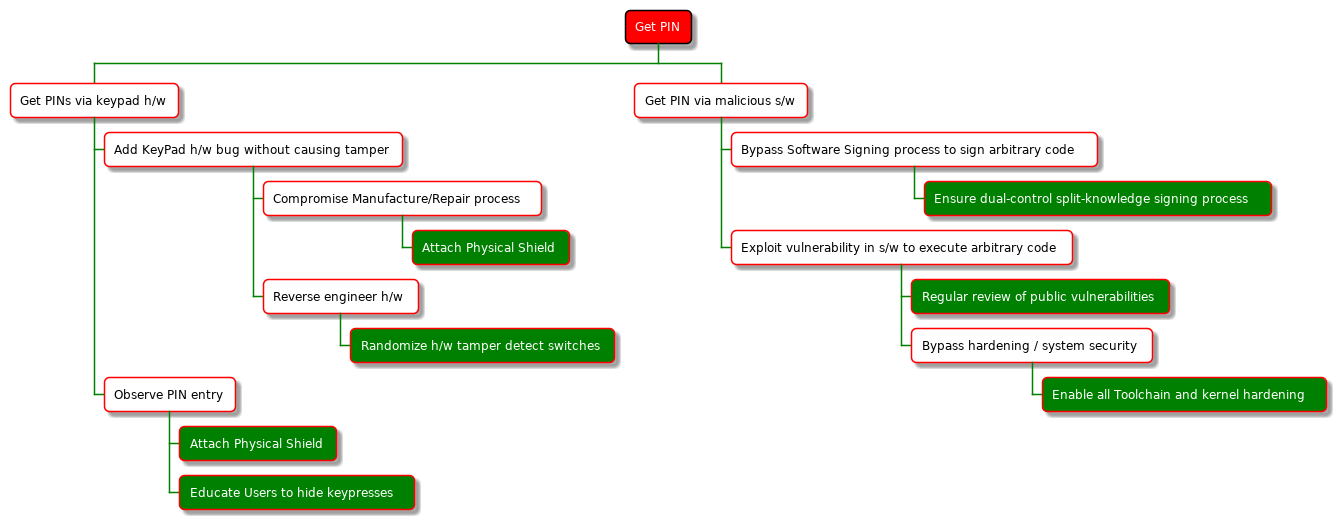
Diagram Source¶
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 | ' ref https://plantuml.com/wbs-diagram
' ref https://plantuml.com/style-evolution for WBS styling
@startwbs
<style>
wbsDiagram {
Linecolor black
arrow {
LineColor green
}
.AttackPath * {
BackgroundColor White
RoundCorner 10
LineColor red
}
' Top of Attack Tree
.AttackTarget {
BackgroundColor Red
FontColor White
RoundCorner 10
}
' Bottom of Attack Tree: * means it applies to everything below the marked node
.CounterMeasure * {
BackgroundColor Green
FontColor White
RoundCorner 10
}
}
</style>
* Get PIN <<AttackTarget>>
** Get PINs via keypad h/w <<AttackPath>>
*** Add KeyPad h/w bug without causing tamper
**** Compromise Manufacture/Repair process
***** Attach Physical Shield <<CounterMeasure>>
**** Reverse engineer h/w
***** Randomize h/w tamper detect switches <<CounterMeasure>>
*** Observe PIN entry
**** Attach Physical Shield <<CounterMeasure>>
**** Educate Users to hide keypresses <<CounterMeasure>>
** Get PIN via malicious s/w <<AttackPath>>
*** Bypass Software Signing process to sign arbitrary code
**** Ensure dual-control split-knowledge signing process <<CounterMeasure>>
*** Exploit vulnerability in s/w to execute arbitrary code
**** Regular review of public vulnerabilities <<CounterMeasure>>
**** Bypass hardening / system security
***** Enable all Toolchain and kernel hardening <<CounterMeasure>>
@endwbs
|